The Of Data Security Services
Table of Contents4 Simple Techniques For Data Security ServicesLittle Known Questions About Data Security Services.Rumored Buzz on Data Security ServicesUnknown Facts About Data Security ServicesData Security Services Can Be Fun For Anyone
Shield of encryption tricks are actually safely stored to shield critical management devices, frequently depending on a secure as well as off-site key to restrain access better. Authentication and certification are actually some of the leading methods to raise information surveillance. You utilize verification to ensure a customer's qualifications coincide as what is in the data bank.Authentication may help calculate what get access to a licensed customer has accessibility. Accessibility command bodies provide the following: Enables accessibility to business resources based on the identity of the user.
All set to take the upcoming action in guaranteeing protection of your mission-critical information? Seek an assessment with a record protection expert.
Getting My Data Security Services To Work
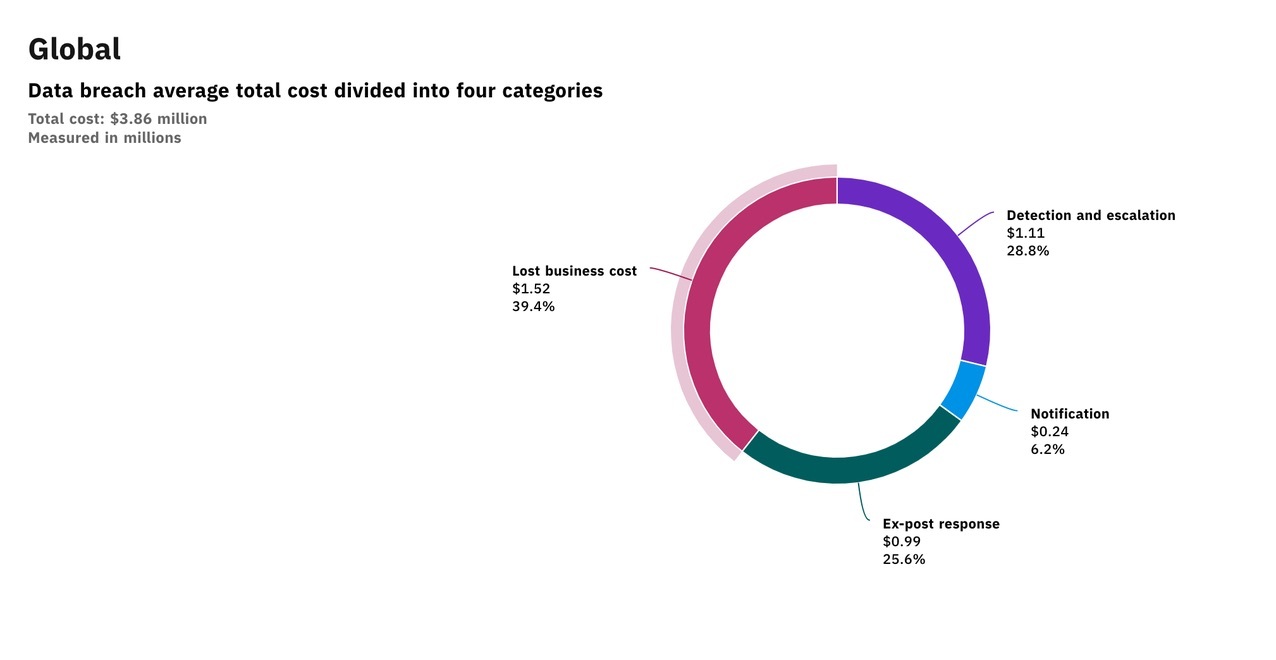
As companies improve their electronic abilities and also begin to perform more company online, cybersecurity and also information protection are actually becoming paramount. Failure to thoroughly get records within a system can easily increase the opportunities of records shadiness or even information fraud, both of which may possess negative monetary outcomes for the influenced business.
For data within a system to be entirely gotten, all information conditions must be encrypted; breakdown to secure all data states leaves it vulnerable to fraud or corruption. The various information states that should be encrypted are: This is actually information that is actually proactively being actually processed through an application; it is being actually improved, looked at, or produced.
This is data that is actually being actually transferred from a sender application to a receiver application. This is the best prone information condition because the data could be simply hijacked or even intercepted just before it gets to the desired recipient This is actually data that is not presently in operation and is kept in a storage till when needed.
7 Easy Facts About Data Security Services Described
Vulnerable relevant information should be actually password defended such that only individuals who understand the security password may access the information. The security password that is utilized to secure the records ought to certainly not be actually utilized for other treatments or even devices; it needs to be actually solid, with a combo of letter, amounts, as well as exclusive personalities, and also distinct.
The security password needs pop over to these guys to be transformed on a normal basis. Among the significant methods to protect your information is actually to moderate the individuals that have accessibility to your system, and by expansion, your data. Access to your network must only be actually provided to individuals who require the applicable information to accomplish their task responsibilities; gain access to must be terminated as quickly as the information in your system is no longer needed to have.
Why is actually data protection necessary? Mostly, it maintains your information secure and constructs assurance amongst your clients - data security services.
Erase records you are actually certainly not utilizing: You need to eliminate both electronic and also bodily duplicates of information you no more requirement. By doing this, you lessen the opportunities of a cyberpunk uncovering it and using it for earnings.
Rumored Buzz on Data Security Services
Veritas 360 data monitoring is actually an excellent device and also may perform the duty of information Protection, Supply, as well as Idea for your information. Having educated and also approved data safety personnel accessible is of fantastic usefulness. An individual on-call that may handle breaches as well as possess a wonderful understanding of institution Sensitive Data Defense.
If there's something that businesses today could be certain approximately, it is actually that corporate information protection can easily not be actually played around. This is actually also the factor why data security tools are actually acquiring traction in the business world. Information is certainly not just an assortment of details that assists businesses determine problems anymore.
Regrettably, this is actually the very reason that cyber dangers versus business data have increased significantly. Essential records protection resources It is actually crucial for companies to bolster their preventative security procedures to survive an atmosphere that is actually link brimming along with cyber dangers, and also ferocious competitors. In this particular short article, our experts will definitely highlight several of the very best kinds of records protection services that every business must carry out to reinforce their corporate surveillance position.
All About Data Security Services
Our team have specified a couple of must-have information safety and security site link resources that can aid your organization protect your delicate data from prying eyes, without overwhelming your IT staff. most ideal information safety and security devices Business networks experience a steady influx of inbound and also outbound visitor traffic as staff members make an effort to access these networks numerous opportunities a time coming from multiple areas - data security services.
These devices encrypt company information in a coded style which may be translated simply through accredited persons after going into the pre-specified protection secret. This confirms advantageous in celebrations where business tools have been actually risked because of theft or hacking. The greatest way to inhibit expert security hazards, in addition to outside undesirable entry to your corporate units and also networks is by restricting accessibility to them.